After an 18 month absence, Q, the mysterious figure whose posts (or “drops”) inspired the QAnon conspiracy movement, has finally returned to posting on 8kun (formerly known as 8chan). However, a number of serious technical errors made at the same time by 8kun’s administrative staff have lifted the veil of anonymity that previously protected Q.
While the site admins’ mistakes don’t let us identify who has posted as Q in the past, we can now authoritatively say that the Q poster who is active in 2022 must be either one of the administrative staff at 8kun or someone working closely with them.
A brief history of Q’s tripcodes
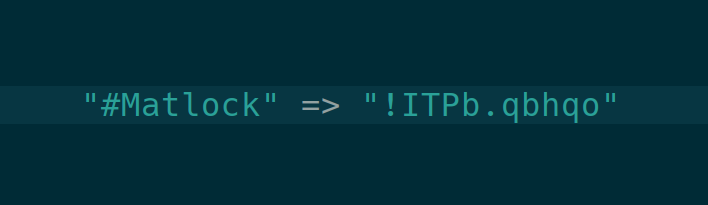
Q’s posts are identified and verified by a tripcode, which is simply a hashed password. This feature, inherited from early anonymous bulletin boards, allows for both user anonymity and for multiple posts to be linked to a single user.
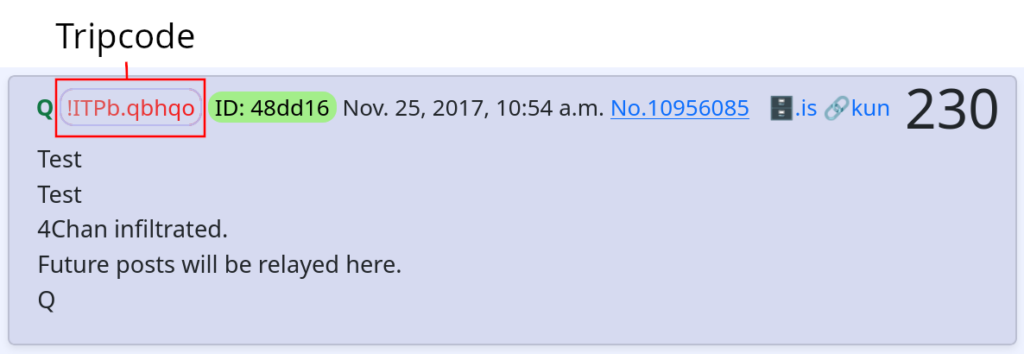
Q began marking posts with 4chan’s simplest, least secure type of tripcode in the 128th drop. Because the simple tripcode algorithm does not use any secret information from the server, and 8chan happened to use the same tripcode algorithm as 4chan, Q’s password produced the same tripcode on 8chan. This allowed Q to migrate to that platform, owned by Jim Watkins, which happened less than a month after the very first Q post.
8chan’s “secure tripcodes”, the style used by Q since 2018, are generated by combining the user’s tripcode password with a “secret salt” (also known as a pepper), which is a secret password hidden on the server, to generate a more secure tripcode. A more secure hash algorithm, SHA-1, is also in use. The addition of a secret salt makes the tripcode password unable to be “cracked” by usual means, unlike their less-secure cousins, which can be cracked fairly easily by duplicating the algorithm on a local computer and making many millions of guesses per second until the password is found. Without knowing the secret salt portion of the input, however, we can’t calculate the outcome of the hash function ourselves and must ask the server.
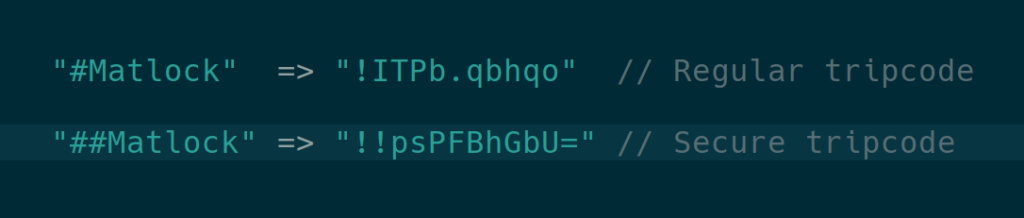
Every one of Q’s insecure tripcodes has now been cracked, and the passwords are now known. However, barring the discovery of a previously unknown weakness in SHA-1, an ordinary user will never be able to crack Q’s current secure tripcode without knowing the secret salt used at the time it was generated.
A hidden exploit
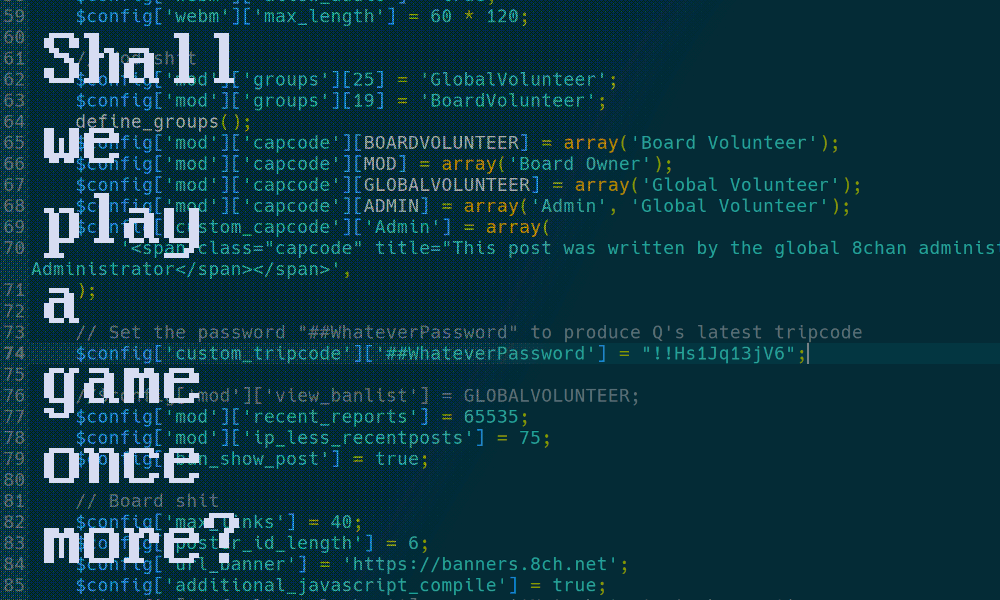
There is a feature called custom_tripcode hidden in plain sight in 8kun’s software that allows for the admins to bypass the normal methods of tripcode generation and make any password of their choosing produce any tripcode of their choosing. This means that 8kun admins, or someone working closely with them, could be using Q’s tripcode without knowing Q’s password.
To test this possibility, we built our own copy of 8kun using the open-source software that powers the site to demonstrate how this feature could be exploited by 8kun administrators in order to pose as Q.
Methodology
8kun is based on open-source software, meaning the source code that powers the website is available for public scrutiny and community contribution. Specifically, it is powered by the open-source imageboard platform OpenIB, a fork of Fredrick Brennan’s infinity project. Knowing all of this, I set out to create a simulated version of 8kun, running on my personal computer, using OpenIB’s source code. I wanted to see for myself exactly what powers the website’s staff have access to.
I had the privilege of receiving technical support from Fredrick Brennan, the original developer of 8chan, on getting a local development version of the OpenIB codebase up and running. The developers have reportedly made additional modifications to the code in a private fork, but the publicly available source was last modified by Ron Watkins on August 25, 2020, just a few months before he resigned as 8kun’s admin. Few or no new features have been introduced to 8kun since Ron’s resignation, suggesting that the open source codebase currently matches the live version of 8kun quite closely.
Getting OpenIB running was at once simple and complex. It involved installing an old, out-of-support version of PHP (5.6) alongside current versions of MariaDB and Apache, running some SQL commands, then debugging some errors in a software stack with which I am wholly inexperienced. But from there, it was clear the software has good bones—considering it was conceived while its principal developer was coming down from a psychedelic drug trip.
With my local development version of 8kun up and running, it was simple to create a few boards, make a few test posts, and then get to the main attraction of this endeavor—testing out the custom_tripcode functionality, something that I had been extremely curious about ever since reading Fred’s description of the feature over a year earlier. It turned out to be exactly as simple as I had visualized it for so long.
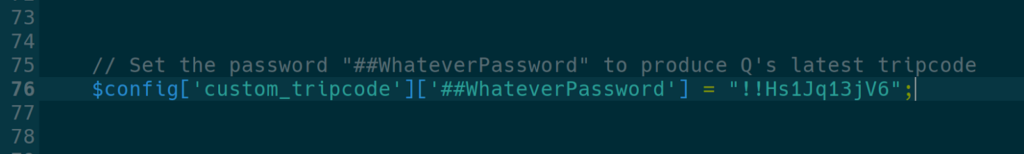
By adding a single line to the file instance-config.php, which controls the site-wide configuration settings, I was able to define an arbitrary password that mapped to Q’s real tripcode and immediately post as Q. It was striking to witness firsthand how incredibly simple it would be for an admin to commandeer the Q persona, and the entire QAnon movement, at the slightest whim.
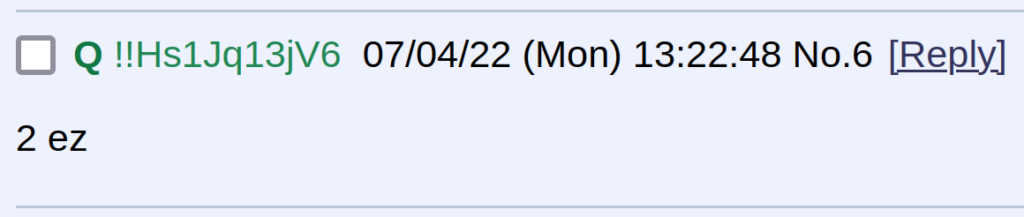
Why does custom_tripcode even exist?
The custom_tripcode feature has existed in the OpenIB codebase since its creation, and was inherited from the infinity (8chan) codebase, which itself inherited the feature from Tinyboard, where it was added on May 24, 2011. It is not clear whether it was ever used before on 8chan / 8kun, but the feature was evidently intended to save time for admins who want a personalized tripcode.
By running the algorithm locally, one can generate millions of tripcodes, which can then be sorted through to find one containing a word or interesting pattern. Ron Watkins, aka “Codemonkey”, used such a tripcode during his tenure as global administrator. His tripcode, “!Odemonkey.” could be used in tandem with a simple “C” in the name field to display his nickname.
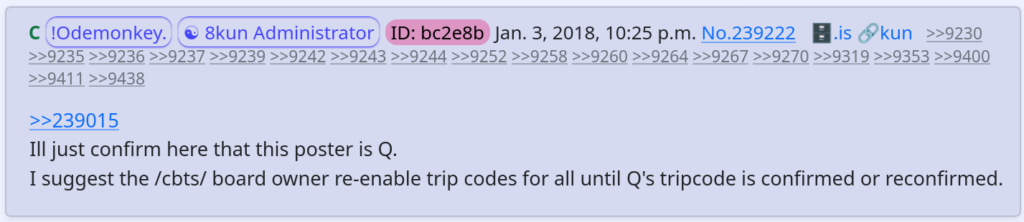
Generating a highly personalized vanity tripcode by brute force could take as long as 12 years on a modern GPU, so the ability for admins to simply define a customized tripcode in the website’s configuration saves a lot of time and energy. However, this virtue has a sinister dual-purpose: it allows an admin to impersonate any tripcode user.
This customized tripcode feature was implemented for basic tripcodes and secure tripcodes, and when an additional “super secure tripcode” feature was added in the final update to the open source codebase in 2020, the custom_tripcode workaround was again updated to work for these tripcodes as well. The update was personally reviewed and accepted by Ron Watkins, proving he remained aware of the feature until his retirement from the site.
How do we know custom_tripcode was used?
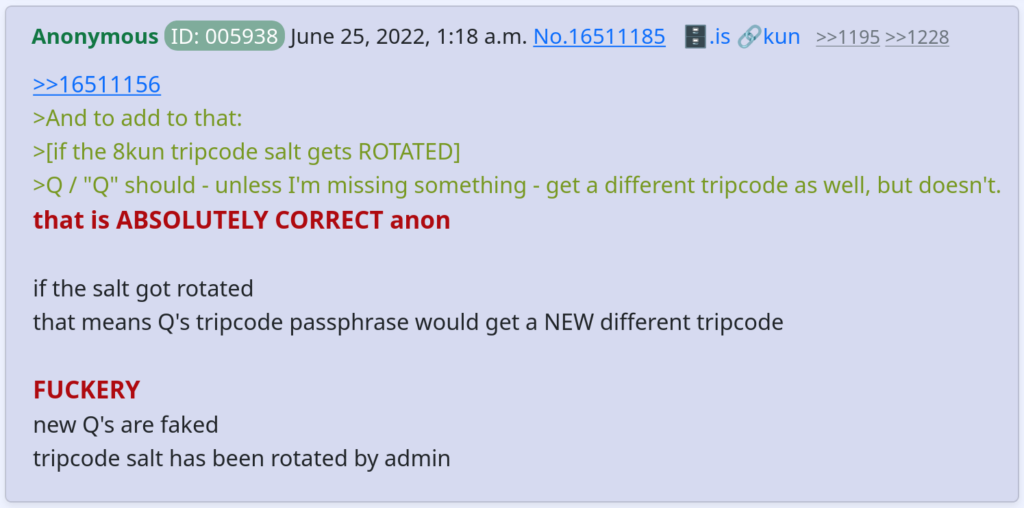
On June 24th, 2022, about two hours before Q posted for the first time in nearly two years, the site’s admins rotated (changed) the secure tripcode salt, in an operation that had not been done since late 2019. Multiple reports from users emerged with complaints that their tripcodes changed, locking them out of their ability to trip post on /qresearch/ and other boards where only pre-approved tripcodes are allowed to be used.
This secret salt is hidden away on the server, only to be modified by the server admin. During “secure tripcode” generation, the secret salt is appended to the user’s tripcode password before hashing. This means that when the secret salt changes, every secure tripcode user’s password will generate a different tripcode from before.
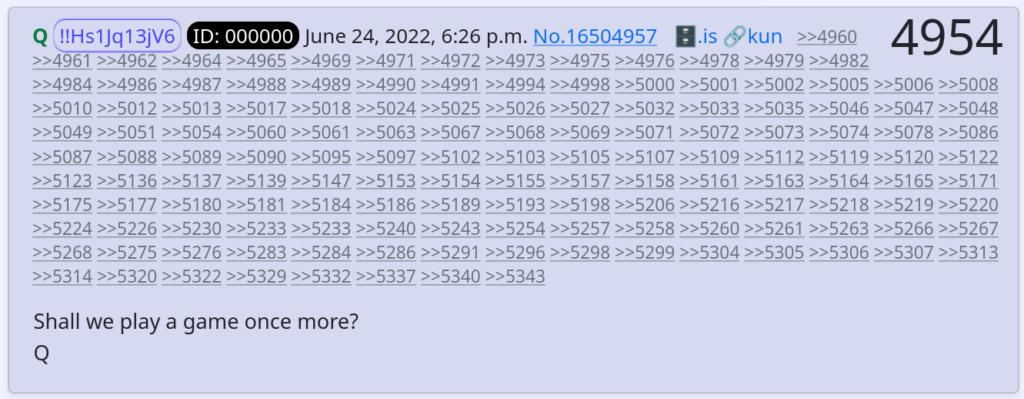
Paradoxically, while all other users’ secure tripcodes changed after the salt rotation, Q’s stayed the same. Since the probability of finding a collision in SHA-1 is less than 1/1020 even knowing the secret salt, this simple observation stands as proof of interference by the server admin, like the use of a custom_tripcode setting or direct modification of the database. It is worth noting that in 2019, Fredrick Brennan predicted and warned about this very possibility, even issuing a direct appeal to Q to use PGP, or another platform-independent method of cryptographically signing posts, instead of just using 8kun-controlled tripcodes. Despite all of this, no measures were ever taken by Q or 8kun staff to ensure that Q would remain platformed in the event of interference by a rogue admin or loss of service. Needless to say, tripcodes were never meant to be used for any serious cryptographic purpose.
Reception from the Q community
After Q went silent on December 8th, 2020, 8kun experienced a lull in activity, but the movement continued without Q. Just as weekly post volume reached an all-time low (barring outages), Q returned, spurring an explosion of new activity on the website.
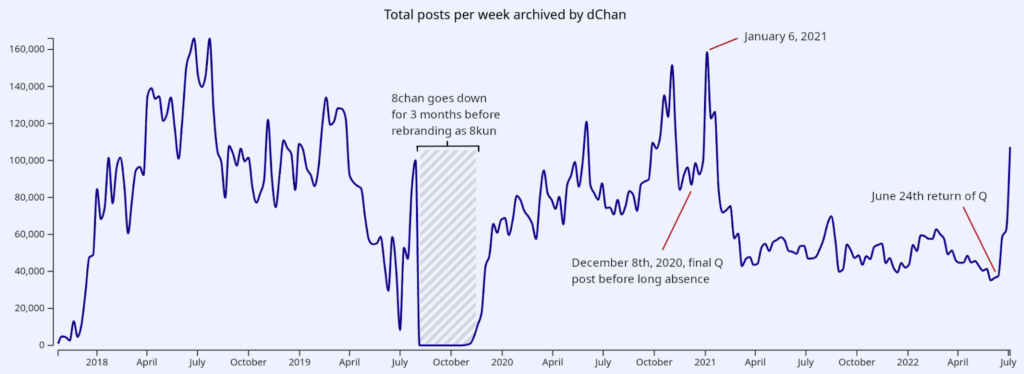
The initial response from the community was overwhelmingly positive, but questions soon emerged about Q’s authenticity in the wake of reports that the secure tripcode salt was rotated.
Processing the facts
We have shown that just hours before Q’s much-anticipated return on June 24th, 2022, 8kun’s configuration was modified in such a way that it became impossible for Q to post with the usual tripcode except by administrative server tampering. Jim Watkins denied these allegations in his official response to mass questioning from his users after these events, instead blaming the actions of his son, the previous admin. However, his own words may speak to the truth of what happened. He explains, “CodeMonkeyZ [Ron Watkins] made a special whitelist for Q before retiring from [8kun]. I don’t know how he did that, but neither [Ron] nor myself are Q.”
A keen reader may notice that the custom_tripcode variable could reasonably be described as a “whitelist”, and such a setting would indeed decouple Q’s password from the normal tripcode generation process. But if the admins aren’t posting as Q themselves, this implies Q’s tripcode password was revealed to the admins and hard-coded in plaintext into the configuration file. As for what purpose such an arrangement would serve to a high clearance level government insider, we find it difficult to conjure any explanation that stands up to the mildest scrutiny.
Previous work by our group has shown that images in Q’s posts originated from UTC+8 and the Pacific time zones. These regions are very broad, but Jim Watkins was known to operate businesses in both and travel regularly between them, prior to being declared an undesirable alien in the Philippines and resettling in California.
Within the Q Origins Project, we have spent many hours of lively discussion trying to figure out what this all means, enumerating all plausible hypotheses that could explain the events of the 24th. There is one explanation that stands out as the simplest and most elegant: acting 8kun admin Jim Watkins, or someone under his employ, modified 8kun’s configuration on the evening of the 24th to allow himself, or a close associate, to post as Q.
We would like to thank Mamie (@MC_Hyperbole), Al Jones (@QOrigins), and Fredrick Brennan (@fr_brennan) for contributions to this article.